Setting up the PoC
A challenge for learning and enjoyment.
The challenge, test out configuring network equipment with three defined methods. (Python3, Ansible, Terraform)
Obviously all of them are closely related. But of course automation tools are there to make our IT jobs easier.
Thinking about this assignment already had me thinking about what I would use without hesitation. The intent of the challenge is to not be guided by experience, but by the tools themselves.
Obviously there will be chances to expand on it. For instance, with Python i would use Jinja, Nornir, Netmiko and more. With Ansible i'll most likely follow a tried and tested route of NetBox and AAP. Terraform is truly the new one here for me, so it will be nice to find out more about it.
PoC
But first we need to build a PoC environment and (re-)define the scope a bit more.
All of the tools require a few things beforehand, expanded it will consist of,
- SSH access
- Management IP's
So essentially a working network o_O with an inventory .. you see where this is going :)
I dont have a lot of networking equipment lying around, nor a bunch of (illegal) Cisco IOS versions. So instead of Physical Equipment, EVE-NG or GNS3, i decided that since it is meant for education to splurge on Cisco Modeling Labs instead. It's only 199us$ right ? ... (Yeah, turns out it wasn't.. Even personal it still required paying Taxes and aside from that the dollar is stronger than the Euro .. so the 200 became 252Euro's o_O )
Regardless, the tool is simple to use, no difficulties whatsoever. And we like it this way :) (path of least resistance)
Network
The network design needs to touch on a few things.
- Be accessible with SSH
- Manageable
- Have Switches, Hosts, Routers
So i came up with this:
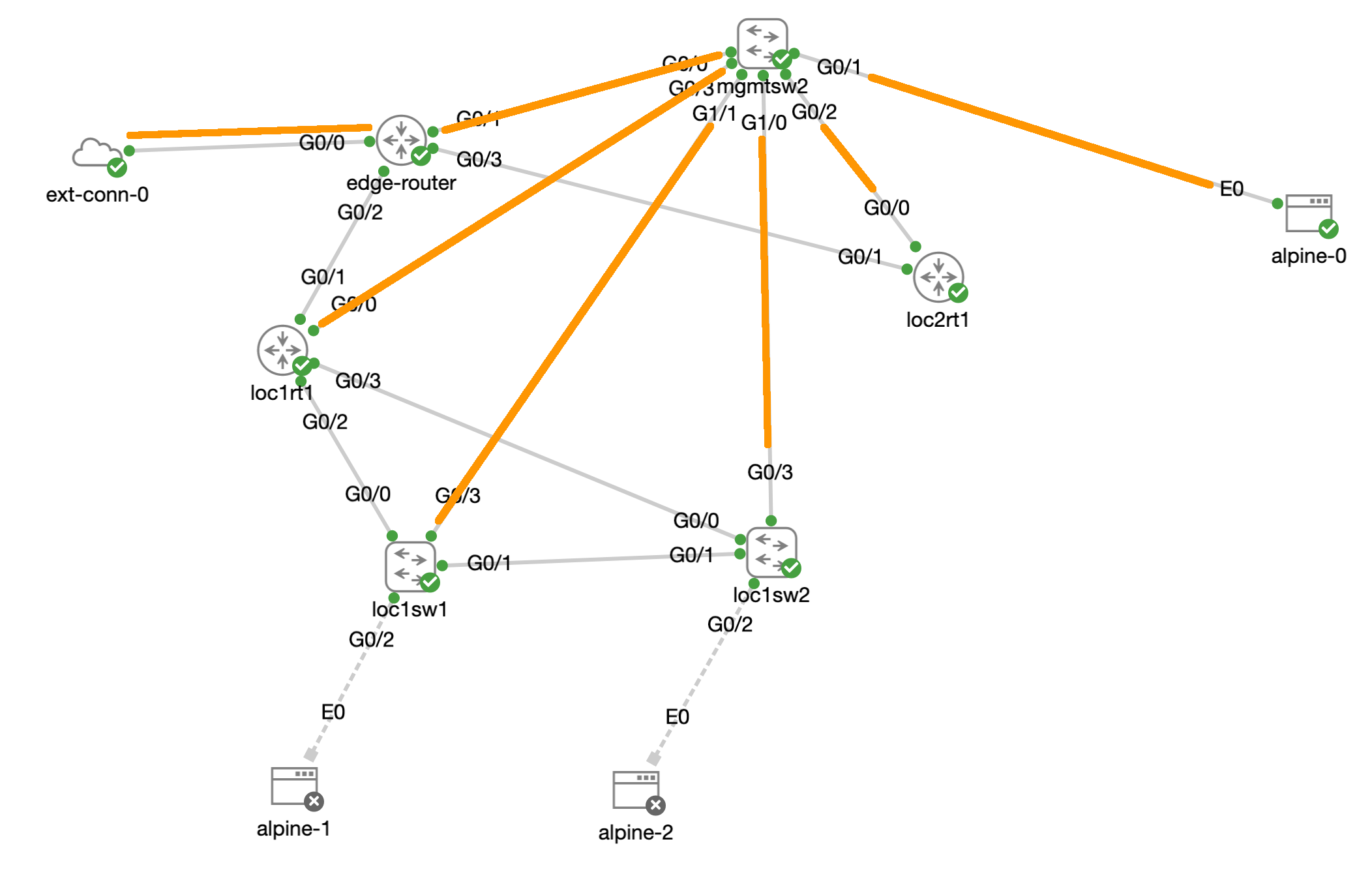
The orange lines are the management links in
- VLAN 2000 management 192.168.4.0/24
With which we will build the inventory.
Default config
The default config for all nodes is:
aaa new-model
service password encryption
service password-encryption
username cisco algorithm-type sha256 secret cisco
enable password 0 cisco
ip domain-name okairi.int
crypto key generate rsa label SSH modulus 2048
ip ssh rsa keypair-name SSH
ip ssh version 2
ip ssh logging events
ip ssh time-out 60
ip ssh authentication-retries 5
line vty 0 4
transport input ssh
exec-timeout 30 0Switches
vlan 2000
name management
! for Karen
int vlan 2000
ip address 192.168.4.XX 255.255.255.0
no shut
ip default-gateway 192.168.4.254
ip route 0.0.0.0 0.0.0.0 192.168.4.254Scope
The network on the outside of the cloud. My physical network is in 192.168.0.0/22. The network on the inside (of CML) is in 192.168.4.0/22. Of which 192.168.4.0/24 is the management LAN.
The 'edge-router' has 192.168.1.17 to outside and 192.168.4.254 to inside. On top of that a DHCP pool is added.
ip dhcp excluded-address 192.168.4.240 192.168.4.255
!
ip dhcp pool management
network 192.168.4.0 255.255.255.0
default-router 192.168.4.254
interface GigabitEthernet0/1.2000
description management
encapsulation dot1Q 2000
ip address 192.168.4.254 255.255.255.0Scope:
- The grey links will need to be configured.
- A routing protocol needs to be added.
- Switches will need to be configured.
- Hosts will need to be able to ping/ssh each other.
So basically the PoC is defined. The time is now to head into the challenge :)
ansible@amane ~/ansible $ ip add | grep 192.168
inet 192.168.1.148/24 brd 192.168.1.255 scope global noprefixroute ens192
ansible@amane ~/ansible $ fping -ga 192.168.4.0/22 2>/dev/null
192.168.4.2
192.168.4.3
192.168.4.4
192.168.4.241
192.168.4.242
192.168.4.254
192.168.4.255
192.168.4.253
ansible@amane ~/ansible $



